Which Best Describes a Byod Bring Your Own Device Plan
Bring this user group out of scope. Bring Your Own Device BYOD Text PDF Webinar Presentation Video.
Pdf Telecharger Byod Policy Pdf Gratuit Pdf Pdfprof Com
The plan also describes the longer-term.

. We can write proofread paraphrase format edit or rewrite your any paper whether its a review or a term paper. Forcing a user group to use an unsatisfactory tool will severely undermine your chance of success especially in the projects early stages. I usually break everything down into three key categories.
Important information for Fanshawe students with disabilities. Ensure your metrics are updated. People places and things.
According to Alex Fullick your best bet is to create a simple plan. Top Hat is a bring your own device BYOD classroom response system that makes use of students personal mobile devices phones tablets laptops as response devices. Switching is easy Set up your device Using the app Sprint Migration Center All get started topics Ways to pay your bill All about your bill Line permissions Your T-Mobile ID Your PINPasscode All account resources topics T-Mobile Network In-flight texting and Wi-Fi Wi-Fi Calling International roaming Mobile Without Borders All network roaming topics Find the.
But best of all they are short which means they can be used for quick tasks that require few materials and little preparation time. BYOD systems offer a number of logistical and pedagogical advantages over traditional clicker-based systems. The increasing prevalence of cloud-based services mobile computing internet of things IoT and bring your own device BYOD in the workforce have changed the technology landscape for the modern enterprise.
Fanshawe College has many accessibility services available for students with any type of accessibility need including non-visible disabilities such as learning disabilities medical conditions and mental illness. High Quality All the papers we deliver to clients are based on credible sources and are quality-approved by our editors. Secure gov websites use HTTPS A lock or https means youve safely connected to the gov website.
Webinar Slides Part 1. If the request for compensation via consultancy is an extortion threat if refused the hacker sells the exploit on the dark web then the motivation is purely. Webinar Slides Part 2.
Share sensitive information only on official secure websites. Participants will work with a template for a sample lesson plan that incorporates. End-user computing improvements will not be valuable to this role without that benefit.
Bring your own device BYOD and access your desktop and applications over the Internet using an Azure Virtual Desktop client such as Windows Mac iOS Android or HTML5. Or you may create a bring-your-own-device BYOD policy and offer training for remote workers to protect your network and data security. This is either gray-hat semi-authorized hacking or black hat non-authorized hacking.
Choose the right Azure virtual machine VM to optimise performance and leverage the Windows 10 and Windows 11 multi-session advantage on Azure to run multiple concurrent user. Bring the benefit in scope.

Pdf Bring Your Own Device Byod An Evaluation Of Associated Risks To Corporate Information Security
What Is Byod Bring Your Own Device Security And Policies

Pdf Telecharger Byod Policy Pdf Gratuit Pdf Pdfprof Com

Pdf Bring Your Own Device A Survey Of Threats And Security Management Models

23 Bring Your Own Device To Work Policy Free To Edit Download Print Cocodoc

23 Bring Your Own Device To Work Policy Free To Edit Download Print Cocodoc

Going Byod Bring Your Own Device Infographic Educational Infographic Byod Bring Your Own Device

Pdf Byod Bring Your Own Device
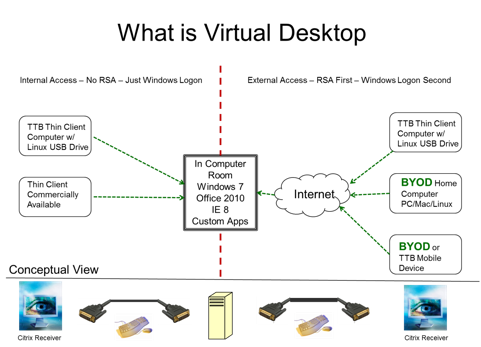
Bring Your Own Device The White House

Pdf Bring Your Own Device Philosophy From The User S Perspective An Empirical Investigation

Pdf A Review Of Bring Your Own Device On Security Issues

Doc Bring Your Own Device Byod To Healthcare Search And Seizure Of Employee And Enterprise Data On Employee Owned Smart Mobile Devices Michael Collins Academia Edu

Pdf A Review Of Bring Your Own Device On Security Issues

What Is Third Party Risk Management By Oguzhan Ozturk Codex Mar 2022 Medium

Bring Your Own Device What Is Byod Ionos

Pdf Security Risk Analysis Of Bring Your Own Device Byod System In Manufacturing Company At Tangerang


Comments
Post a Comment